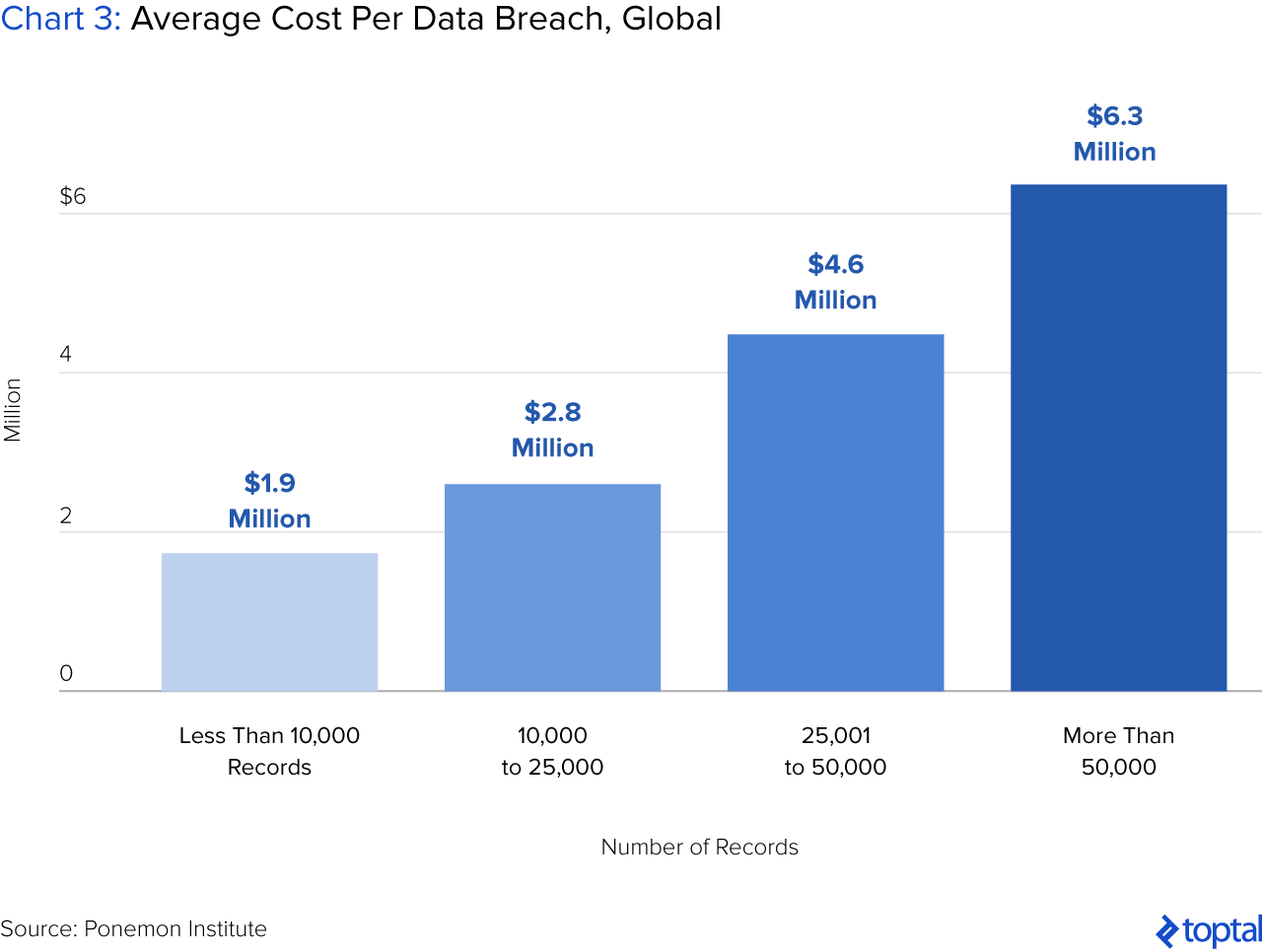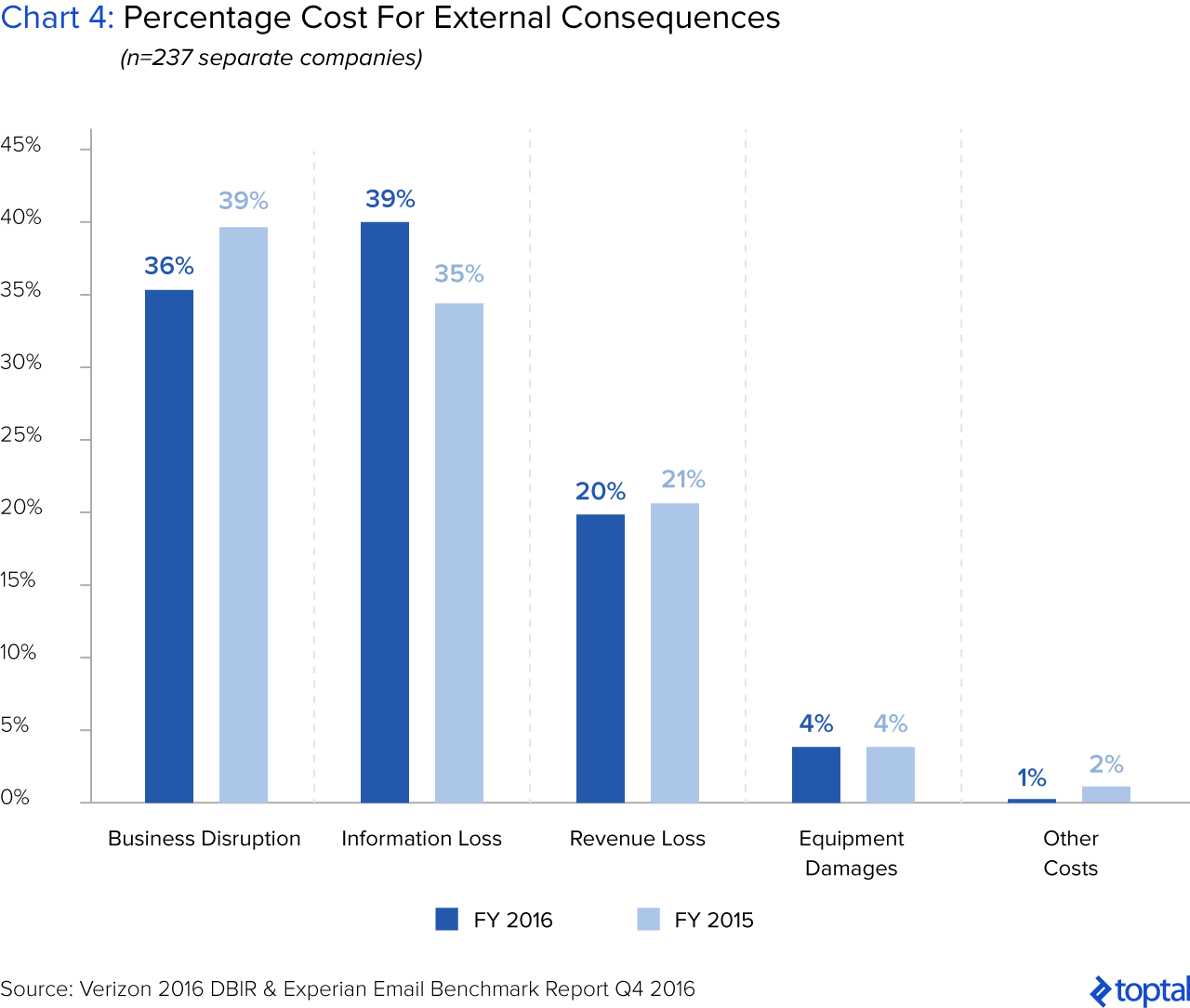“Think of [cybersecurity] more as safety and security in roads and cars. The car hasn’t really changed in the last 30 years, but a lot of security is built in, and it’s not sexy until the moment it saves your life. You’ve got bits that are hidden – airbags – and bits there to remind you to be safe like seatbelts…Some of it is about good behaviour and good attitude, some of it is about physical security to remind you there is a risk, and some of it is baked in to save you.”
– Sian John, Senior Cybersecurity Strategist at Symantec
We’ll admit it. Cybersecurity isn’t sexy. However, in today’s digital age, cybersecurity has become increasingly critical for large corporations and small startups alike. Today, the stakes are higher than ever, as “every company has become a tech company.” Technology has become more than a supplement to a company’s operations, and in many cases, the assets living on their network aretheir core operations. This is compounded by the fact that hacks are becoming commonplace due to the rise of mobile usage and internet of things, as well as the growing ecosystem of cybercriminals.
This article outlines the types of cybercriminals, cybercrime tactics, and contributing factors. The piece also includes tangible solutions companies can use to protect themselves. Solutions include both technological safeguards and human components. For example, leadership must recognize cybersecurity as a strategic business problem and not just an “IT problem.” In addition, some of the most effective solutions are fairly basic, such as employee education or two-factor authentication for users.
What Is Cybercrime?
Put simply, cybercrime is a crime with some kind of computer or cyber aspect to it. It can take shape in a variety of formats, and from individuals or groups with different motivating factors. Cyber threats are fundamentally asymmetrical risks in that small groups of individuals can cause disproportionately large amounts of damage.
Categories of Cybercriminals
- Financially motivated organized crime groups: Most of these groups are located in Eastern Europe
- Nation-state actors: People working directly or indirectly for their government to steal sensitive information and disrupt enemies’ capabilities. They are generally the most sophisticated cyber attackers, with 30% originating in China.
- Activist groups, or “hacktivists”: Are not usually out to steal the money. They’re out to promote their religion, politics or cause; to impact reputations or to impact clients.
- Insiders: These are the “disillusioned, blackmailed, or even over-helpful” employees operating from within a company. However, they may not engage in cybercriminal activities intentionally; some might simply take a contact list or design document without realizing the harm it could cause.
The average age of a cybercriminal is 35, and 80% of criminal hackers are affiliated with organized crime. In short, people choose this as a profession.
Cybercrime Tactics
Cybercriminals utilize both static and dynamic methods to commit their crimes. Let’s delve in.
Distributed Denial of Service (DDoS)
A DDoS attack attempts to disrupt a network’s service. Attackers send high volumes of data or traffic through the network until it becomes overloaded and stops functioning. The incoming traffic flooding the victim originates from many different sources, potentially hundreds of thousands. This makes it impossible to stop the attack by blocking a single IP address, and makes it difficult to distinguish legitimate traffic from attack traffic.
Phishing
Often posing as a request for data from a trusted third party, phishing attacks are sent via email and ask users to click on a link and enter their personal data. It often involves psychological manipulation, invoking urgency or fear, fooling unsuspecting individuals into handing over confidential information.
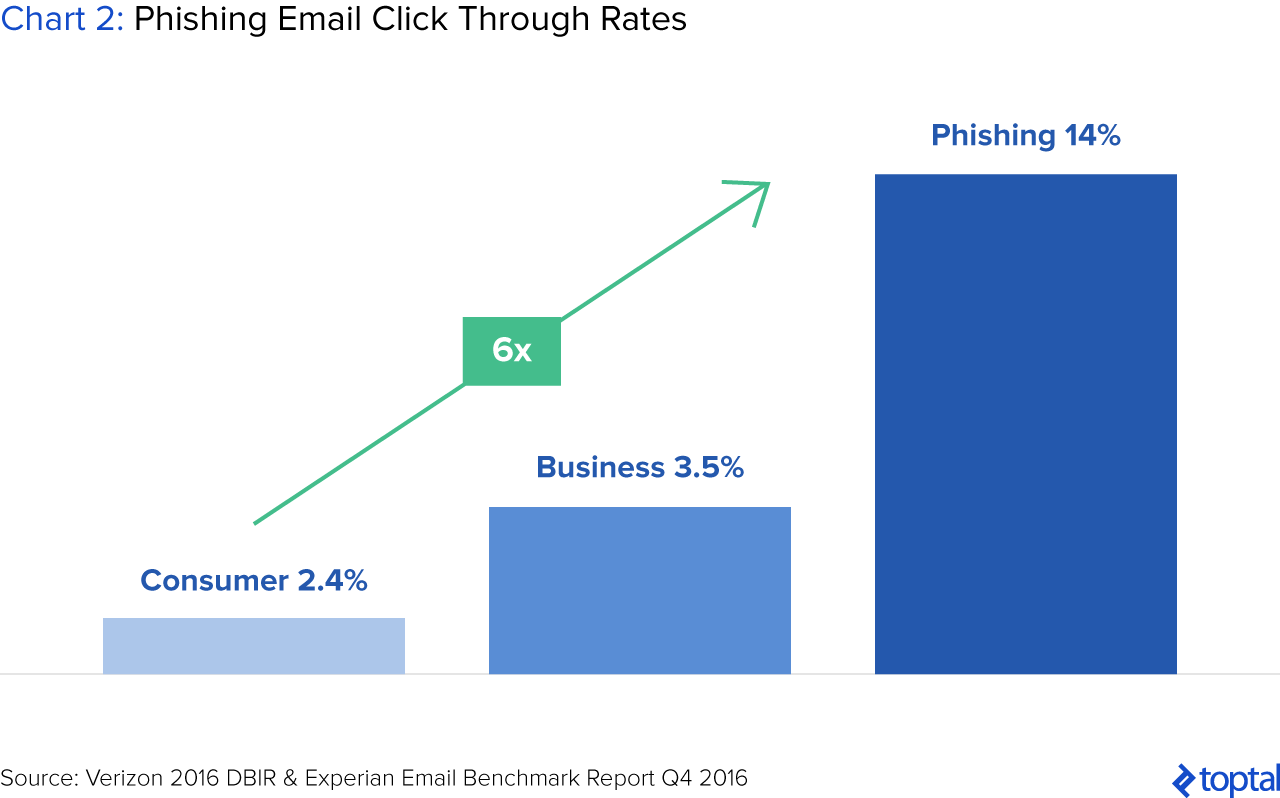
There are a couple concerning factors. First, phishing emails have become sophisticated and often look just like legitimate requests for information. Second, phishing technology is now being licensed out to cybercriminals, including on-demand phishing services and off-the-shelf phishing kits. Perhaps most concerning is the fact that dark web services have enabled cybercriminals to refine their campaigns and skills. In fact, phishing emails are six times more likely to be clicked than regular consumer marketing emails.
Malware
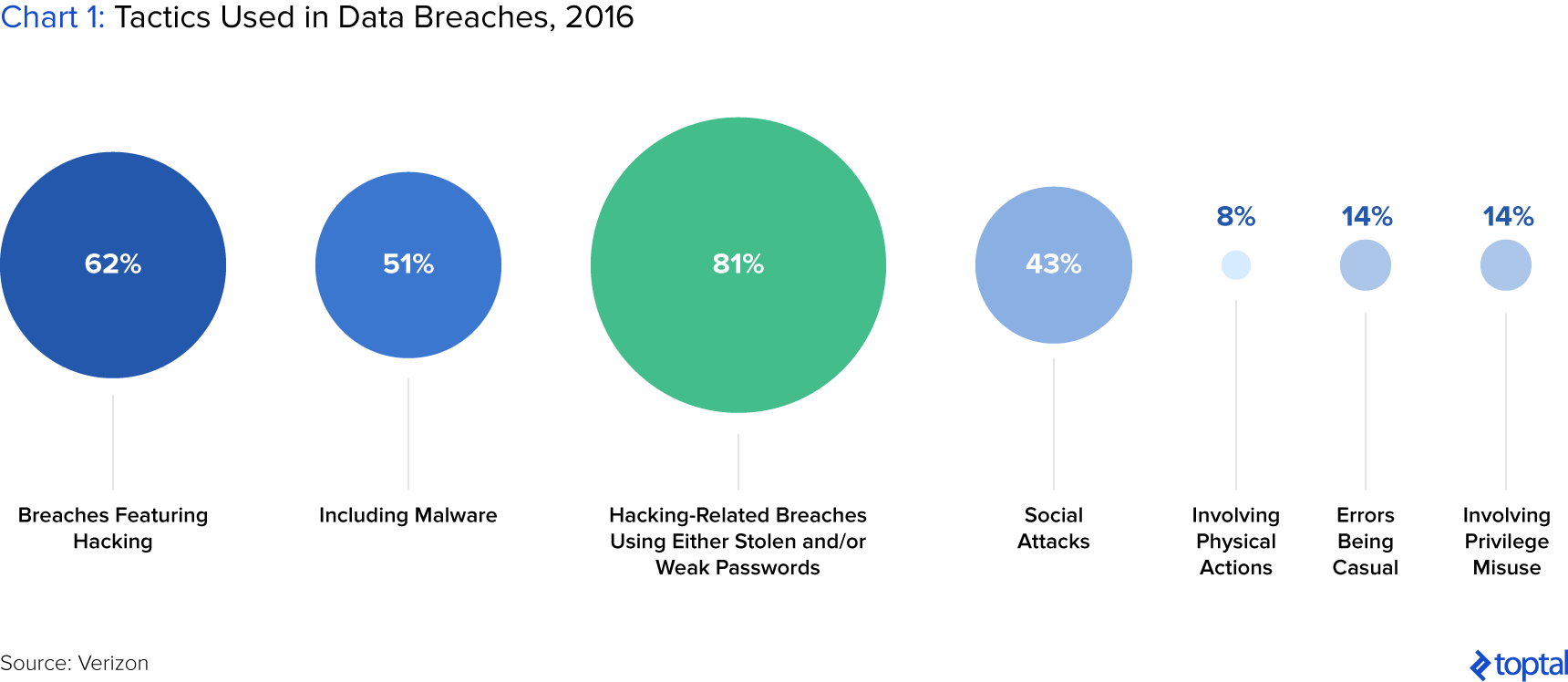
Malware, short for “malicious software,” is designed to gain access or damage a computer. Malware is an umbrella term for a host of cyber threats including Trojans, viruses, and worms. It is often introduced to a system through email attachments, software downloads, or operating system vulnerabilities.
Internal Privilege Misuse
While the malicious insiders who leak information to WikiLeaks receive all the press and glory, a more common scenario is that an average but opportunistic employee or end-user secretly takes confidential data hoping to cash out somewhere down the line (60% of the time). Sometimes, employees get a little too curious and do some snooping (17%). Personal information and medical records (71%) are targeted for financial crimes, such as identity theft or tax-return fraud, but sometimes it’s simply for gossip.
Physical Card Skimmers
These attacks include physically implanting on an asset that reads the magnetic stripe data from a payment card (e.g., ATMs, gas pumps, POS terminals). It’s relatively quick and easy to carry out an attack like this, with the potential for relatively high yield—and so is a popular action type (8%).
Cybersecurity Consequences and Costs
Costs to Firms
Three years ago, the Wall Street Journal estimated that the cost of cybercrime in the US was $100 billion. Other reports estimated that the figure was as much as ten times higher than this. In 2017, the average cost of a data breach is $7.35 million, compared to $5.85 in 2014. Costs include everything from detection, containment, and recovery to business disruption, revenue loss, and equipment damage. Beyond monetary concerns, a cyber breach can also ruin intangibles, such as a company’s reputation or customer goodwill.
Interestingly, companies with the highest levels of business innovation often have costlier attacks. A “business innovation” could be anything from an acquisition or divestiture to entry into a new geographic market. A company acquisition or divestiture was shown to increase the cost of cybercrime by 20% while the launch of a significant new application increased the cost by 18%.
For financial services firms, the costs after a security breach can be attributed to business disruption, information loss, revenue loss, and other costs.
Cybersecurity Is Pronounced for the Financial Services Industry
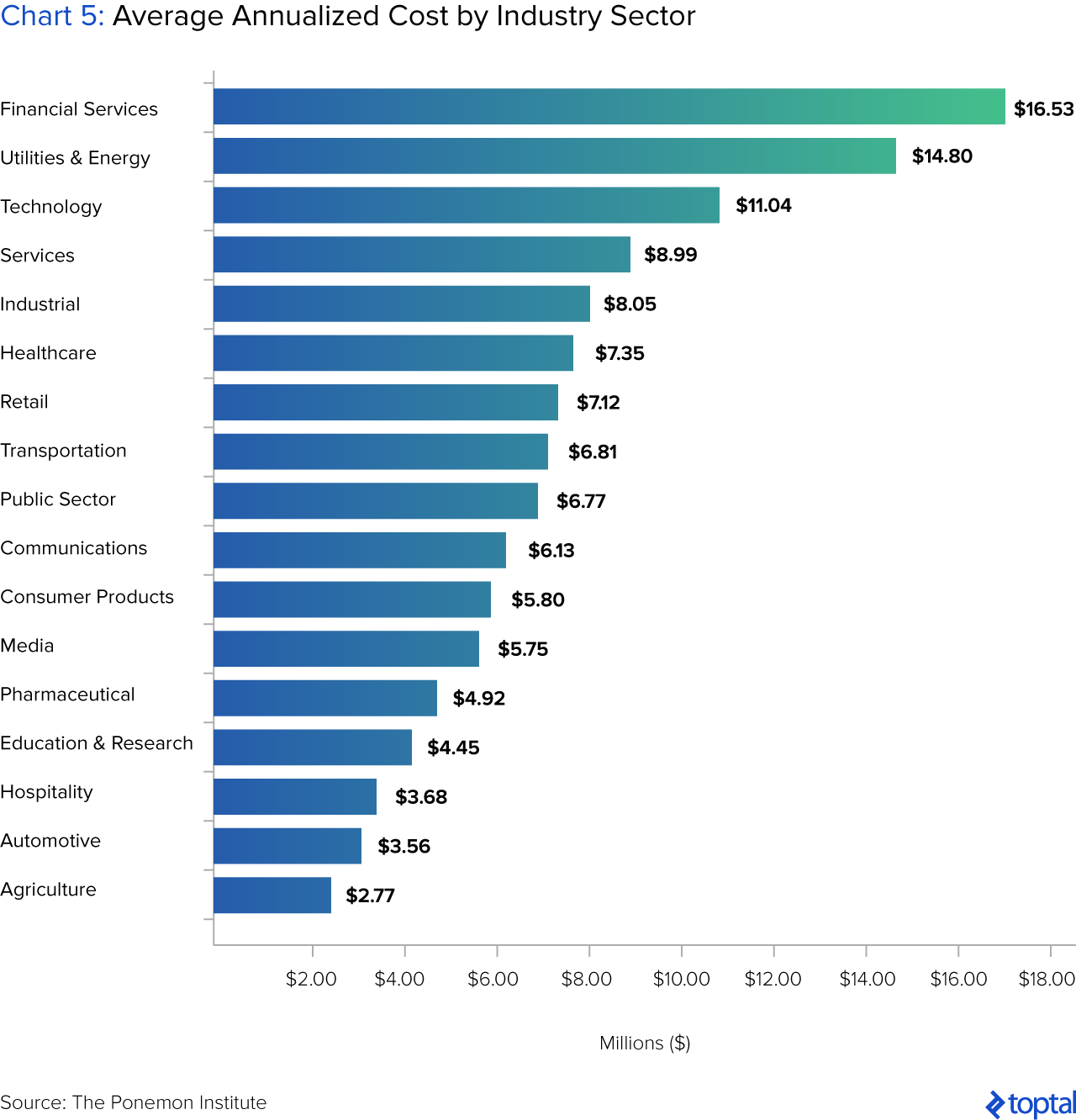
The unfortunate truth is that, while no industry is immune, cybersecurity issues are particularly pronounced for financial services. According to the 2017 Verizon Data Breach Investigations Report, 24% of breaches affected financial organizations (the top industry), followed by healthcare and the public sector. For comparison, in 2012, the industry was ranked third, after the defense and the utilities and energy industries. Beyond frequency, the cost to finance firms are the highest of all industries, losing an average of $16.5 million in 2013.
In financial services, the most common type of cyber breach involved DDoS attacks. And, as for all DDoS attacks, the finance industry was hit the hardest.
Famous Financial Services Hackings
Attack on Six American Banks (2012)
In 2012, six major American banks (Bank of America, JPMorgan Chase, Citigroup, U.S. Bank, Wells Fargo, and PNC) were targets in a wave of computer attacks by a group claiming Middle Eastern ties. The attacks caused internet blackouts and delays in online banking, resulting in frustrated customers who could not access their accounts or pay bills online.
These were DDoS attacks, where the hackers overwhelmed the bank websites to the point of shutdown. The attacks also utilized botnets, networks of infected computers that do the bidding of criminals. Sometimes, botnets are referred to as “zombie computers” that obey the commands of a “master botnet.” Unfortunately, these can be rented through black markets or lent out by criminals or governments.
JPMorgan (2014)
In summer of 2014, in the largest security breach of an American bank to date, the names, addresses, phone numbers, and email addresses of around 83 million accounts were compromised by hackers. Ironically, JPMorgan spends around $250 million on computer security every year. The 2014 breach was not the result of a sophisticated scheme. The attack did not use a zero day attack, the novel software bug that sells for millions in the black market. It also did not utilize malware that hackers in North Korea employed in their cyberattack of Sony. Rather, the source of the issue was basic: The bank did not employ two-factor authentication, which is an additional layer of security when users sign in to access data or an application. JPMorgan’s security team neglected to upgrade one of its network servers with the dual password scheme—that’s all it took.
SWIFT Payment System (2016)
In February 2016, the Society for Worldwide Interbank Financial Telecommunication (SWIFT), an international consortium of over 11,000 banks that facilitates cross-border transfers, was hacked. The Bangladesh Bank, a user in the SWIFT network, was hacked in the amount of $81 million. Only a small proportion was recovered before the Federal Reserve Bank of New York blocked in 30 other transactions that might have transferred an additional $850 million.
These attacks show that payment networks are only as trustworthy as their weakest link. Many in the industry were not surprised by the attack. According to Justin Clarke-Salt, co-founder of Gotham Digital Science, a cybersecurity company, the attacks exploited a weakness in the system: that not every institution protects access to SWIFT in the same way. After all, “Attackers often attack people who are easier to attack…So far from what we know has been publicly reported, they have very much targeted smaller financial institutions. This is probably because they have less sophisticated controls.”
Are Small or Large Firms More Vulnerable?
Though the news often covers attacks on the largest corporations (Target, Yahoo, Home Depot, Sony), small companies are not immune. In the last 12 months, hackers have breached half of all small businesses in the United States, according to the 2016 State of SMB Cybersecurity Report.
On one hand, some argue, smaller companies may not be able to recover from a cyber attack**. **According to Sian John, senior cybersecurity strategist at Symantec, companies hit with a security issue experience a “massive reputational and financial hit” for companies in the year afterwards, before returning to normality. She questioned, “If you’re a smaller company, can you survive that dip?”
On the other hand, others argue, small companies are at an advantage: “A big company is more vulnerable than a small company: They have big data pools and hundreds of people have to have access…If you are at the smaller end of the scale, being smart about business processes and understanding where those business processes might be exploited is easier than for a large organisation,” declared Richard Horne, partner at PricewaterhouseCoopers.
Cybersecurity Challenges
Factors Contributing to the Rise in Cybercrime
A “Corporate” Breed of Cybercriminals Has Emerged
Cybercriminals are now adopting corporate best practices to increase the efficiency of their attacks. Some of the most enterprising criminals are selling or licensing hacking tools to less sophisticated criminals. For example, professional criminals have been selling zero-day technology to criminals on the open market, where they are quickly commoditized. Gangs also offer ransomware as a service, which freezes computer files until the victim meets the monetary demands, and then take a cut for providing the license.
There is now an entire ecosystem of resources for cybercriminals to leverage. “Advanced criminal attack groups now echo the skill sets of nation-state attackers. They have extensive resources and a highly-skilled technical staff that operate with such efficiency that they maintain normal business hours and even take the weekends and holidays off…We are even seeing low-level criminal attackers create call centre operations to increase the impact of their scams,” said Kevin Haley, director at Symantec.
Security of Third-Party Vendors
If a third party gets hacked, your company is at risk of losing business data or compromising employee information. For example, the 2013 Target data breach that compromised 40 million customer accounts was the result of network credentials being stolen from a third-party heating and air conditioning vendor. A 2013 study indicated that 63% of that year’s data breach investigations were linked to a third-party component.
Increased Use of Mobile Technologies by Customers
Due to a growing number of online targets, hacking has become easier than ever. In consumer banking, usage of mobile devices and apps have exploded. According to a 2014 Bain & Company study, mobile is the most-used banking channel in 13 of 22 countries and comprises 30% of all interactions globally. In addition, consumers have adopted mobile payment systems. For banks competing with fintech startups, customer convenience will remain important. They may have to weigh the potential fraud losses with losses from a more inconvenient user experience. Some institutions are utilizing advanced authentication to confront these added security risks, allowing customers to access their accounts via voice and facial recognition.
Proliferation of Internet of Things (IoT)
Internet of things (IoT) is devoted to the idea that a wide array of devices, including appliances, vehicles, and buildings, can be interconnected. For example, if your alarm rings at 7:00 a.m., it could automatically notify your coffee maker to start brewing coffee for you. IoT revolves around machine-to-machine communication; it’s mobile, virtual, and offers instantaneous connections. There are over one billion IoT devices in use today, a number expected to be over 50 billion by 2020. The issue is that many cheaper smart devices often lack proper security infrastructure. When each technology has high risk, the risk grows exponentially when combined.
Cybersecurity Awareness vs. Readiness to Address
Despite headlines around cybersecurity and its threats, there remains a gap between companies’ awareness and their readiness to address it. In the last year, hackers have breached half of all US small businesses. In the Ponemon Institute’s 2013 survey, 75% of respondents indicated that they did not have a formal cybersecurity incident response plan. 66% of respondents weren’t confident in their organization’s ability to recover from an attack. Further, a 2017 survey from cybersecurity firm Manta indicated that one in three small businesses don’t have the tools in place to protect themselves.
Tactically speaking, financial services companies have much to improve in terms of detecting and responding to attacks. In 2013, 88% of the attacks initiated against FS companies are successful in less than a day. However, only 21% of these are discovered within a day, and in the post-discovery period, only 40% of them are restored within a one-day timeframe.
Cybersecurity Solutions Require a Multi-pronged Approach
There isn’t a “one-size-fits-all” solution to cybersecurity. However, in general, solutions should include both sophisticated technology and more “human” components such as employee training and prioritization in the boardroom.
Actionable Threat Intelligence
Real-time Intelligence:
Real-time intelligence is a powerful tool for preventing and containing cyber attacks. The longer it takes to identify a hack, the more costly its consequences. A 2013 study by the Ponemon Institute revealed that IT executives believe that less than 10 minutes of advance notification of a security breach is sufficient time to disable the threat. With just 60 seconds’ notification of a compromise, resulting costs could be reduced by 40%.
According to James Hatch, director of cyber services at BAE Systems, “Detecting [a cyber attack] early is key…It could be the difference between losing 10% of your [computers] and 50%.” Unfortunately, in reality, on average it takes companies more than seven months to discover a malicious attack.
Complementary Actions:
Companies can take several smaller, tactical steps to protect themselves. These include:
- Enacting a multi-layered defense strategy. Ensure that it covers your entire enterprise, all endpoints, mobile devices, applications, and data. Where possible, utilize encryption and two- or three-factor authentication for network and data access.
- Performing a third-party vendor assessment or creating service-level agreements with third parties: Implement a “least privilege” policy regarding who and what others can access. Make it a habit to review the use of credentials with third parties. You could even take it a step further with a service level agreement (SLA), which contractually obligates that third parties comply with your company’s security policies. Your SLA should give your company the right to audit the third party’s compliance.
- Continuously backing-up data. This can help to safeguard against ransomware, which freezes computer files until the victim meets the monetary demands. Backing up data can prove critical if your computers or servers get locked because you wouldn’t need to pay for access to your data.
- Patching frequently. A software patch is a code update in existing software. They are often temporary fixes between full releases of software. A patch may fix a software bug, address new security vulnerability, address software stability issues, or install new drivers.
- Whitelisting software applications. Application whitelisting would prevent computers from installing non-approved software. This allows administrators to have much more control.
Anti-hacker Insurance
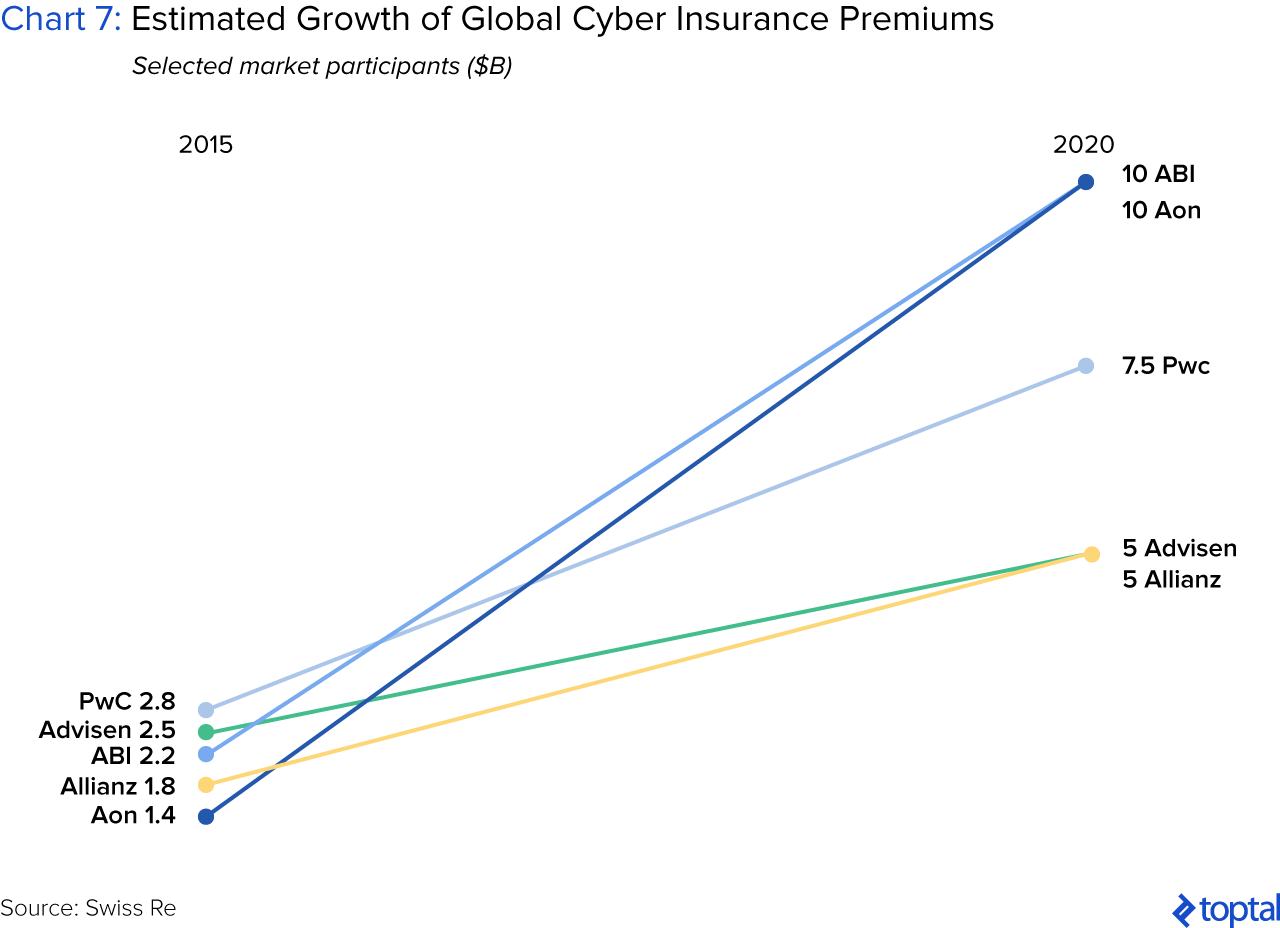
An emerging trend is anti-hacker insurance, or cyber-insurance. Its scope varies across providers, but typically protects against security breaches and losses. Insurers typically limit their capacity to between $5 million and $100 million per client. As of October 2016, only 29% of US business had purchased cyber-insurance. However, the overall cyber-insurance market is estimated to be $20 billion by 2025, up from $3.25 billion today. Insurers are bullish, estimating that premiums will triple over the next few years.
For an organization to determine how much cyber insurance it needs, it should measure its cyber risk. It must understand how their assets are impacted by a cyber attack and how to prioritize them.
Bug Bounty Programs
Another new idea in the industry is something called a bug bounty program, where an organization pays outsiders (“friendly hackers”) to notify it of security flaws. Companies ranging from Google and Dropbox to AT&T and LinkedIn have already adopted this practice.
Don’t Forget the Human Component
- An “IT problem” becomes a strategic business problem. For many CEOs and CFOs, hacking can be frustrating because they don’t understand the enemy. According to Richard Anderson, chairman of the Institute of Risk Management, “There are still a lot of people sitting astride larger companies who still regard it as something the geeks look after, rather than it being a business issue.” However, as the statistics have demonstrated, this could not be further from the truth.A Deloitte white paper suggests creating a dedicated cyber threat management team and creating a “cyber risk-aware culture.” It is also recommended that organizations designate a chief information security officer (CISO). For example, neither JPMorgan nor Target had CISOs when they were breached in 2014 and 2013, respectively.
- Back to basics: Employee training. Data breaches are often the result of humans’ psychological weaknesses. It’s therefore critical to educate your employees about the warning signs of security breaches, safe practices (being careful around opening email attachments, where they are surfing), and how to respond to a suspected takeover.
Parting Thoughts
A common rebuttal to the increasing attention to the dangers of cybersecurity is, “What, then? Are we just supposed to stop innovating for fear of attacks?” The answer is, not exactly. However, it could be helpful for companies to view cybersecurity as a matter of ethics. That is, cybersecurity should not merely be a matter of technology, but one of morality as well. After all, is it ethical to create and sell technology that leaves consumers vulnerable? With Silicon Valley’s “growth or die” and sometimes short-sighted culture, this is likely an unpopular attitude.
However, there is precedent in other sectors. For example, the American Medical Association and American Bar Association require professionals to follow their respective ethical codes. Doctors must pledge the Hippocratic oath, one of the oldest binding documents in history, which mandates that doctors vow to protect their patients. Similarly, lawyers follow a Model Rules of Professional Conduct, vowing to protect and respect their clients.
We’d all do well to remember that though technology may come and go, right and wrong never changes.
Originally posted on Toptal