Cybersecurity in today’s connected world is a fundamental component of any enterprise. Weak security practices can result in a major service disruption and/or data breach. So, when it comes to safeguarding your business and possibly that of your customers from cyber-attack, you want the most effective tools for threat detection, response and reporting at your disposal.
Here, we look at six top apps designed to keep networks, websites and wireless devices secure from would-be hackers and their malice.
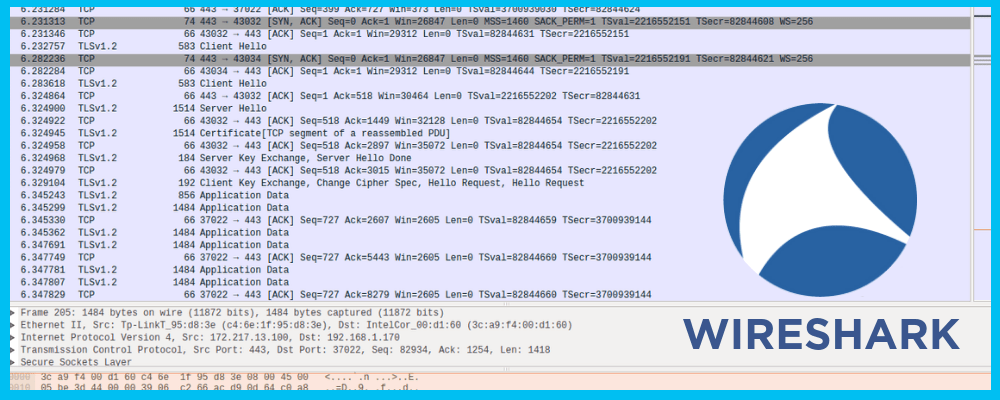
1. Wireshark
The first step in vulnerability assessment is to have a clear picture of what is happening on the network. Wireshark is a network protocol analyzing tool that works to capture specific traffic, such as communication between two internet protocol (IP) addresses or Domain Name System (DNS) queries on a network, at a microscopic level to provide a broad and lucid view of activity.
Because Wireshark is relatively user-friendly, it is the standard across many commercial and non-profit enterprises, government agencies, and educational institutions. It is typically used to look for stray IP addresses and suspicious activity from a single IP address. The traffic data generated by Wireshark can be dumped into a file to be reviewed at a later time.
2. Nmap
Nmap, short for network mapper, has been a popular free tool among network administrators for more than a decade. Its longevity can be largely attributed to its effectiveness in providing network discovery and security auditing. Nmap can scan to a granular level to determine what conversations are being had between IP addresses on a network. It’s also useful in detecting remote devices and, in many cases, firewalls, routers, and their make and model.
A network administrator can use Nmap to check which ports are open on a system, and if those ports can be exploited in simulated attacks. It also works to identify what services a computer is running for network inventory purposes and managing service upgrades. All are vital in implementing a sound cybersecurity strategy.
3. Metasploit
Once discovery and scanning are done using tools such as Wireshark and Nmap, it’s time to go to the operating system and application level. Metasploit is a powerful open source framework that performs rigorous scans against a set of IP addresses.
Unlike many other frameworks, it can also be used for anti-forensics by the IT team. Code is written to attempt to exploit a particular vulnerability. It’s then tested with Metasploit to see if the vulnerability gets detected. This process can technically be reversed as well. If a virus attacks using some unknown vulnerability, Metasploit can be used to test the patch for it.
4. Entersoft Apps
Ensights is a relatively new security assessment tool launched by Entersoft to help guard a company’s apps against the latest and most devastating cyber attacks. Entersoft is known for providing tools that go beyond penetration testing to delve deep into backend database and infrastructure security analysis, code review, application-programming interface (API) threat modeling, and more.
5. Websecurify
Websecurify also brings application-level security testing into play. Websecurify can scan dozens of pages of web applications to traverse code and find loopholes, such as insecure passwords and physical file paths in libraries, swiftly. Screenshots of problem areas can be created automatically, which helps in preparing audit reports. Websecurity is one of the few platform-independent tools and also supports mobile application coding.
6. Aircrack-ng
Modern infrastructure contains wireless devices in the data center as well as in the corporate environment to facilitate the use of mobile devices. Aircrack-ng is a suite of tools created to assess different areas of wireless security for such things as misconfiguration and the use of over-simplified passwords that can leave a WiFi network open to attack.
Not Familiar with These Apps?
Systems and networks have become so complex and are frequently updated, making it difficult for personnel to maintain a level of threat detection and response adequate to safeguard business interests. To help organizations keep up with the learning curve and the times, Cybint Solutions offers customized cyber education and training solutions across the cyber security spectrum.